Why would we provide a free hour of our Cybersecurity Consultant’s time to discuss your cybersecurity posture? Because we want to prove that we are right for your business.
Adaptive Compliance Cyber Readiness Evaluation
Proactive evaluations are a company’s best defense against cyberattacks.
All organizations maintain sensitive information that is increasingly subject to attacks by malicious cyber actors. A cyber attack not only leads to potential data loss, but can significantly alter business operations and brand reputation, and detrimentally impact efforts to comply with regulatory standards. In order to prevent future costly breaches and combat evolving threats, it is vital for organizations to understand their cyber risk profile by identifying existing vulnerabilities and recognizing the current cyber threat environment.
Adaptive Compliance Cyber Readiness Evaluation services will proactively identify your organization’s cyber risk profile. Our team of cybersecurity experts provides recommendations using a set of expertly-developed methodologies, tools, and techniques to identify vulnerabilities and system misconfigurations and to improve your organization’s overall cyber posture.
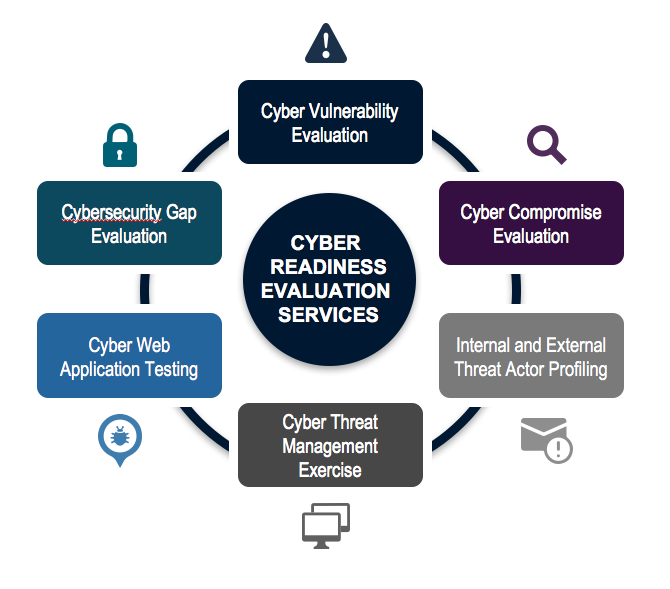
Cyber Vulnerability Evaluation
Locate existing vulnerabilities that can be exploited by malicious actors. These vulnerabilities included people, process, and technology.
Internal and External Threat Actor
Review systems configurations, data access policies and standards to determine opportunities for internal and external threat actors to access sensitive corporate or other protected information.
Cyber Threat Management Exercise
Create and conduct a cyber threat simulation exercise that enables executives and staff to build practical experience responding to cyber threats.
Cyber Web Application Testing Evaluate the incident response and cyber protection controls through an approved and targeted cyber attack.
Cybersecurity Gap Assessment
Identify cybersecurity gaps and the overall state of the company’s cybersecurity framework following industry best practices and standards from the International Organization for Standardization (ISO), National Institute of Standards and Technology (NIST) or COBIT 5, and mapping to the NIST CyberSecurity Framework.

